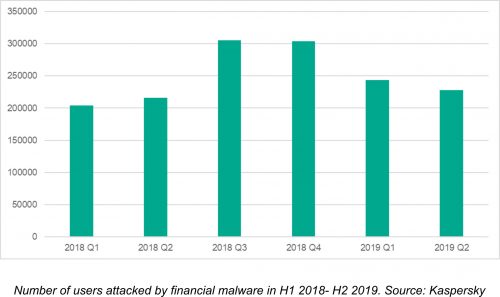
Kaspersky researchers have discovered 430,000 users faced malware aimed at stealing finances, cryptocurrencies, and web-money services in the first half of 2019 – seven percent more than in the same period last year. Over a third (30.9%) of those affected are corporate users – double the figure discovered in the first half of 2018 (15.3%).
Financial malware, commonly identified as banking Trojans, is aimed at stealing finances and financial data, as well as providing threat actors with access to users’ and financial organizations’ assets and machines. Such threats have always occupied a significant part of a threat landscape, as finance is the most common motivation for cybercriminals and fraudsters. Kaspersky data on new samples of these threats constantly demonstrates that malware aimed at stealing funds is active and extremely dangerous, especially when it comes to corporate environments – since most corporate networks usually rely on connected devices, and if one is compromised then the whole entity may be under threat.
Typical attack vectors for malware are spam emails and phishing web pages. The latter usually appear to be legitimate websites, yet in fact are created by threat actors in an attempt to steal credentials, bank card details or other types of sensitive information. During the first half of 2019, Kaspersky researchers have detected more than 339,000 phishing attacks from web pages disguised as landing pages of large banks.
The researchers have also compiled a list of the most popular banking Trojan families that were used to attack corporate users. Four-in-ten (40%) financial threats on corporate users came from the RTM banking Trojan – one of the most dangerous types of banking malware for businesses in 2018. RTM is followed by the Emotet banking Trojan at 15%. This threat can be particularly damaging as once it gets inside the entity’s network perimeter, it can self-distribute through vulnerabilities in unpatched devices and then download extra threats onto the victim’s device. The Trickster banking Trojan rounds up the top three identified malware, with 12% of discovered threats.
For private users, the situation was found to be different. The list of malware that attempted to attack them is topped by Zbot malware (26%), which steals credentials with the option of remote control by threat actors, followed by RTM and Emotet (both mentioned above). Interestingly enough, in 2018 RTM was almost entirely aimed at organizations, while figures from the first half of 2019 show that this malware is now reaching a significant share of ordinary, domestic users.
“We expect to see a rise in the number of attacked users in the second half of 2019. Usually, we see a rise in malicious activity after the holiday season, when people are using their devices less than usual and therefore are less likely to fall a victim to threat actors. We urge everyone to be extra careful with all banking and finance-related operations that they perform online and remain vigilant,” said Oleg Kupreev, security researcher at Kaspersky.
To protect your business from financial malware, Kaspersky security specialists advise:
- Introducing cybersecurity awareness training for your employees, particularly those who are responsible for accounting, to teach them how to distinguish phishing attacks: do not open attachments or click on links from unknown or suspicious addresses
- Installing the latest updates and patches for all of the software you use
- Forbidding the installation of programs from unknown sources
- For endpoint level detection, investigation and timely remediation of incidents, implement EDR solutions such as Kaspersky Endpoint Detection and Response. It can catch even unknown banking malware
- Integrating Threat Intelligence into your SIEM and security controls in order to access the most relevant and up-to-date threat data
Kaspersky recommends private users:
- Always install security updates as soon as possible
- Do not install software from unknown sources. In the case of mobile platforms – turn this option off in the settings menu
- Use a reliable security solution, such as Kaspersky Total Security